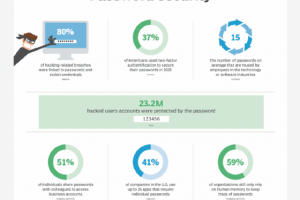
What is a passkey? A passkey is an alternative method of user authentication that eliminates the need for usernames and passwords. Rather than relying on old login methods that are susceptible to... Read more »

The Bank of England regulator, the Prudential Regulation Authority (PRA), has highlighted a number of concerning gaps and limitations in how major insurers model and respond to cyber risk, after conducting a... Read more »
Security teams are warned to be on the lookout for a growing wave of opportunistic and largely untargeted cyber attacks exploiting two related exploit chains to target Microsoft Exchange servers. This is... Read more »
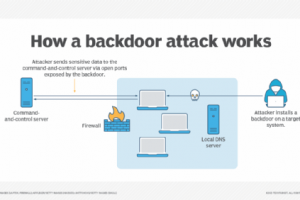
What is a backdoor? A backdoor attack is a way to access a computer system or encrypted data that bypasses the system’s customary security mechanisms. A developer may create a backdoor so... Read more »

Veteran web company Yahoo! has emerged as the most imitated brand in phishing attacks over the last three months of 2022, according to Check Point’s quarterly Brand phishing report, which highlights the... Read more »

Trellix and GitHub have collectively fixed a total of 61,895 open source projects that were found to be susceptible to a 15 year-old path traversal vulnerability in Python’s tarfile module. The firm’s... Read more »

From The Tinder Swindler to Inventing Anna, true crime documentaries and dramatisations found a prominent place in popular culture in 2022. The Netflix specials captivated audiences’ attention and curiosity about identity fraud,... Read more »

Under-resourced charities running services and fundraising activities online are increasingly seen as a soft touch by cyber criminals looking to make a quick buck, and are at risk of malicious actors taking... Read more »

Royal Mail has said that international deliveries of letters and parcels are getting back on track after being suspended for over a week in the wake of a suspected LockBit ransomware attack,... Read more »

Most IT leaders (83% ) think there’s an “availability gap” between how quickly they need systems to be recoverable and how soon that can be achieved. Meanwhile, 81% identify a “protection gap”... Read more »
