
Officials from Ukrainian cyber agency the State Service of Special Communications and Information Protection (SSSCIP) and its European Union (EU) counterpart, the EU Agency for Cybersecurity (ENISA), have held high-level talks in... Read more »
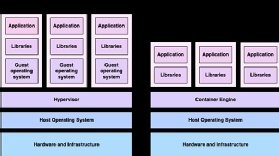
Containers have quickly become a fundamental part of DevOps. Their lightweight and portable nature makes them attractive to all sizes of organisation, from small startups trying to reduce costs to large multibillion-pound... Read more »
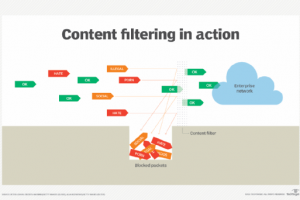
What is a filter in computing? The term filter in computing can mean a variety of things, depending on the technology or technical discipline in question. There are four distinct applications for... Read more »

Proposals in the Online Safety Bill to give the telecoms regulator Ofcom powers to mandate technology companies to use scanning software to monitor encrypted messages for illegal content should be dropped, it... Read more »

The air gap is a fundamental concept of storage and backup. Essentially, it means to have a physical or logical disconnect between production systems and the location of secondary data, including backups.... Read more »
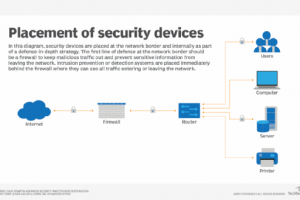
What is network security? Network security encompasses all the steps taken to protect the integrity of a computer network and the data within it. Network security is important because it keeps sensitive... Read more »

Cloud platforms, as a remotely managed service, come with a service-level agreement (SLA) that guarantees an uptime percentage or your money back. These SLAs, and the shifting of responsibility of infrastructure maintenance... Read more »

Three Spanish nationals have been extradited from Spain to France to face charges that they supplied EncroChat encrypted phones that were used by organised crime groups. French public prosecutors argue that the... Read more »
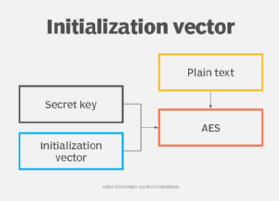
What is an initialization vector (IV)? An initialization vector (IV) is an arbitrary number that can be used with a secret key for data encryption to foil cyber attacks. This number, also... Read more »

The Francis Crick Institute has hundreds of global partnerships that require controlled access to sensitive health data. Its current CIO is James Fleming, who joined the research institute four years ago. Fleming,... Read more »
