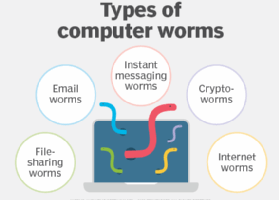
What is a computer worm? A computer worm is a type of malware whose primary function is to self-replicate and infect other computers while remaining active on infected systems. A computer worm... Read more »

It takes an average of just three steps for a threat actor to infiltrate a target cloud environment and get to its “crown jewel” assets, and as a result, vast numbers of... Read more »

Researchers at Secureworks’ Counter Threat Unit (CTU) have warned of a new and potentially serious vulnerability affecting the pass-through authentication (PTA) hybrid identity authentication method used in Azure Active Directory (AD). PTA... Read more »

Internal Cisco data leaked late last week by the China-based Yanluowang ransomware operation has been confirmed as stolen during a cyber attack earlier in 2022, but has insisted the leak poses no... Read more »

TA453, an Iran-aligned advanced persistent threat (APT) group, is going to increasingly complex lengths to compromise its targets, adopting a technique informally known as multi-persona impersonation (MPI) in the social engineering playbook... Read more »
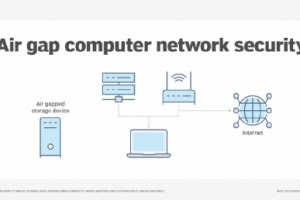
What is an air gap? An air gap is a security measure that involves isolating a computer or network and preventing it from establishing an external connection. An air-gapped computer is physically... Read more »

If you pay attention to cloud security, you may have heard about a new category of security tools called data security posture management, or DSPM. These tools ensure sensitive data always has... Read more »
Blogs How Spend From the Mobile phone Gambling enterprises Functions Can i Be Capable Spend Because of the Cellular phone In which We Alive? Discounts Profile and Cds Download The Software To... Read more »

Fifteen months after a “velvet divorce” from previous partner FireEye, the acquisition of cyber defence, threat intelligence and incident response services specialist Mandiant by Google has formally completed on 12 September. Valued at... Read more »

Although the global economy faces troubled times, we can expect no pause in cyber threats and attacks, so CISOs must direct investment towards technologies to protect customer-facing and revenue-generating workloads, and should... Read more »
