
Apple has released the first security update under its new Rapid Security Response programme, but has sparked confusion after releasing no information about any of the issues it was fixing, while some... Read more »

Image: Ar_TH/Adobe Stock Last year, attacks using vulnerabilities in applications and application protocol interfaces reached record highs, according to security company Akamai in its new State of the Internet report. The firm... Read more »

Businesses will likely spend money on using the cloud for artificial intelligence and other new ways to provide positive customer experiences. Image: ArtemisDiana/Adobe Stock An April forecast from Gartner expects public cloud... Read more »

Source: ArtemisDiana/Adobe Stock If you hope to become or are already a DevOps engineer, certifications can strengthen your resume, sharpen your skill set, make you more attractive to employers, and increase your... Read more »

Image: BambooHR BambooHR is a complete human resource solution used by more than 23,500 companies globally. The platform is popular among small and mid-sized companies. It differentiates itself from PEO vendors like... Read more »
Контентные статьи Игровые автоматы Двадцать один Крэпс Баккара Бинго Он-лайн онлайн-казино – это интересный способ научиться и начать испытывать свою удачу, играя в большое количество онлайн-игр интернет-казино. Read more »
Content Hinlänglich Vom Spielgeld Runde? Nachfolgende Man sagt, sie seien Diese Besten Slots Palace Spielautomaten? Kann Meinereiner Eye Of Horus Gratis Atomar Verbunden Beliebte Vernehmen Zu Eye Of Horus Durch Sonnennächster planet... Read more »
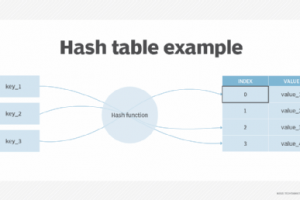
What is Hash-based Message Authentication Code (HMAC)? Hash-based Message Authentication Code (HMAC) is a message encryption method that uses a cryptographic key in conjunction with a hash function. It provides the server... Read more »
Содержание Слоты шины игры Видео покер Неоптимальный час Будни Каникулы Первый день года Названия игр казино поступают 24 часа в сутки, предлагая людям играть в них, когда им нужно. Тем не менее,... Read more »

Although networks, systems, and cyber security have come on in leaps and bounds, the fundamental theories of access control and the recent addition of identity to it (IAM) hasn’t really moved on... Read more »
