
Although networks, systems, and cyber security have come on in leaps and bounds, the fundamental theories of access control and the recent addition of identity to it (IAM) hasn’t really moved on... Read more »

The UK Cyber Security Council has launched the first phase of a certification mapping tool designed to help developing cyber professionals map all available security certifications onto 16 previously identified specialisms –... Read more »
With days to go until the coronation of King Charles III, cyber fraudsters are seeking to capitalise on a surge in public interest, according to researchers at Kaspersky, who have uncovered multiple... Read more »
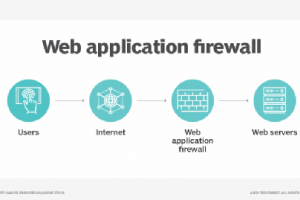
What is a web application firewall (WAF)? A web application firewall (WAF) is a firewall that monitors, filters and blocks Hypertext Transfer Protocol (HTTP) traffic as it travels to and from a... Read more »

The government is playing a high-stakes game of chicken with technology companies by being “intentionally ambiguous” about the impact legislation going through Parliament that could undermine end-to-end encryption, a peer has claimed.... Read more »

The security community is being invited to explore the potential of generative artificial intelligence (AI) to act as a useful tool in its research efforts, with the release of a number of... Read more »
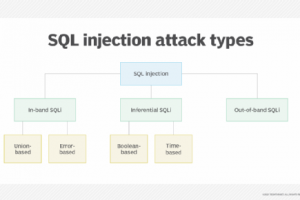
What is a SQL injection (SQLi)? A SQL injection (SQLi) is a technique that attackers use to gain unauthorized access to a web application database by adding a string of malicious code... Read more »

Google Cloud has fixed a potentially dangerous application programming interface (API) vulnerability in its platform that, had it been exploited by malicious actors, could have led to widespread data breaches across multiple... Read more »

Security researchers at managed detection and response (MDR) specialist eSentire have revealed how they are turning the tables on an expansive cyber crime operation that has lured in thousands of people working... Read more »

Researchers at WithSecure have issued an alert after uncovering evidence that a notorious cyber criminal gang is exploiting a recently disclosed vulnerability in Veeam Backup & Replication data backup and recovery software... Read more »
