
WithSecure researchers have exposed a network of fraudulent YouTube videos, channels and associated web applications that are manipulating users into joining dodgy cryptocurrency investment scams. The fraud operation appears to be promoting... Read more »

Per Ploug, open source tech lead at Spotify, has worked in open source for many years and, having watched its evolution, he believes that companies are now far more aware about “open... Read more »

The global recession has many people – and companies – putting on warm sweaters as they turn down their thermostats. On the ground level, that means more people pinching pennies and looking... Read more »

Russian state sponsored hackers have become increasing sophisticated at launching phishing attacks against critical targets in the UK, US and Europe over the past 12 months. Threat actors have created fake personas,... Read more »

The Home Office’s independent review of the Investigatory Powers Act (IPA) will assess whether safeguards on the way the police and intelligence agencies acquire and use bulk databases on UK citizens are... Read more »

Cyber security leaders tend to be happy with the quality of threat intelligence they get from their industry partners, but struggle to generate real insight from it and are making uninformed, or... Read more »
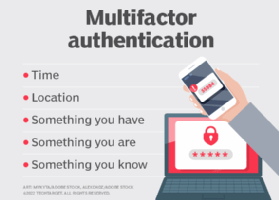
What is passwordless authentication? Passwordless authentication is signing into a service without using a password. This is often done with certificates, security tokens, one-time passwords (OTPs) or biometrics. Passwordless authentication is generally... Read more »
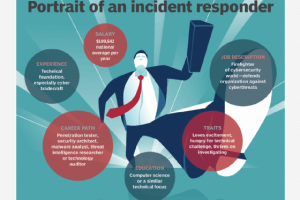
An incident response career path might be the answer for anyone who loves information security and thrives on excitement and technical challenges. The explosion of cyberthreats means that incident responders — sometimes... Read more »

The Russian hacktivist collective Killnet has carried out a series of distributed denial of service (DDoS) attacks against Nato, causing temporary disruption to some of the military alliance’s public-facing websites. The Killnet... Read more »

A former Royal Bank of Scotland (RBS) worker who blew the whistle on lax data protection practices at the bank faces storing sensitive information under her bed indefinitely as a second regulator... Read more »
