
The NHS’s national data guardian for health and social care, Nicola Byrne, has today issued fresh guidance addressing the question of what is meant by “public benefit” and how health and social... Read more »

Ethical hackers working through HackerOne programmes discovered more than 65,000 software vulnerabilities in 2022 – 21% up on 2021 – and over 120,000 customer vulnerabilities, with reports for vulnerability types introduced by... Read more »

Microsoft has rounded off 2022 with a typically light Patch Tuesday for December, with a total of 52 patches addressing six critical vulnerabilities and two zero-days of lesser severity. The two zero-day... Read more »
Registers of Scotland, or RoS, is one of the longest established public records services in Britain and Ireland, with land data held in its Register of Sasines – sasine being an ancient... Read more »

The year 2022 has been unabating in the number of high-profile breaches and cyber criminal gangs, on top of nation-state actors, participating in geopolitical conflicts. Companies across industries, including those in energy,... Read more »

The European Union (EU) – United States (US) Data Privacy Framework has taken a step closer to reality after the European Commission (EC) issued a draft data adequacy decision – ruling that... Read more »

The role of the chief information security officer (CISO) is in a state of flux, with changing dynamics such as increasing levels of risk and threat, more stringent regulation and compliance, making... Read more »
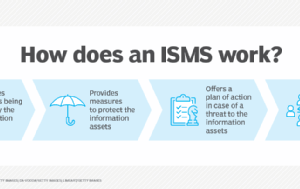
What is ISO 27001? ISO 27001, formally known as ISO/IEC 27001:2022, is an information security standard created by the International Organization for Standardization (ISO), which provides a framework and guidelines for establishing,... Read more »

Finland has launched a voucher-based scheme to help companies embrace best practice systems to reinforce their IT network and information security defences. The Information Security Voucher (ISV) scheme was rolled out on... Read more »

A new data breach of Uber employee email addresses, internal documents and information relating to its IT estate – specifically its mobile device management (MDM) platform – may have originated via a... Read more »
