
The UK’s cyber security community descended en masse on a central London venue on 12 October to celebrate the 2022 Security Serious Unsung Heroes Awards, which recognised champions of diversity and mental... Read more »

What is a clean desk policy (CDP)? A clean desk policy (CDP) is a corporate directive that specifies how employees should leave their work space when they leave the office. Most CDPs... Read more »

Growth in end-user cyber spending is being driven by the increase in remote and hybrid working models, the ongoing transition from virtual private networks (VPNs) to zero-trust network access (ZTNA) and the... Read more »

The UK’s National Cyber Security Centre (NCSC) has today published new guidance to encourage organisations to work in tandem with others in their supply chains to identify and address security issues, following... Read more »

French Supreme Court rejects EncroChat verdict after lawyers question secrecy over hacking operation
France’s Supreme Court has referred a criminal case that relies on evidence from the hacked EncroChat encrypted phone network back to the court of appeal after finding that prosecutors failed to disclose... Read more »

Microsoft has issued fixes for a total of 85 newly discovered common vulnerabilities and exposures (CVEs) in its October Patch Tuesday drop, among them a single zero-day vulnerability, but has not yet... Read more »
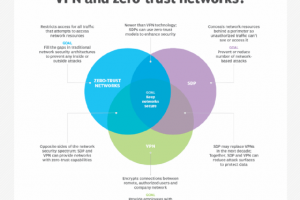
In organizations with remote employees, productivity depends on secure, reliable access to applications, services and data over the internet from any device at any location or time. Yet, the internet can expose... Read more »
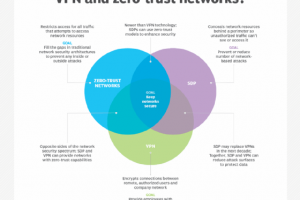
In organizations with remote employees, productivity depends on secure, reliable access to applications, services and data over the internet from any device, at any location or time. Yet the internet can expose... Read more »

In a see-sawing economy, it can be difficult to determine how best to invest, which is why Forrester’s latest Planning guide 2023: Security and risk report is seen as providing a much-needed... Read more »

Japanese automaker Toyota and its tech subsidiary Toyota Connected have been forced to issue an apology after discovering that a contractor had left source code relating to its T-Connect services publicly exposed... Read more »
