
The Netherlands Forensics Institute (NFI) is part of Uncover, a project aiming to help law enforcement agencies track criminal digital messaging. Since the encrypted communication network EncroChat was dismantled, criminals have been... Read more »
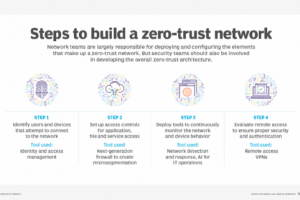
Perimeter security is no longer the best option for enterprise IT departments. A far more flexible architecture is needed that focuses on users, devices and services. The concept of zero trust was... Read more »

The pace of life seems to be ever increasing as technology and software tries to keep up with the real and perceived demands of users. This race to get out the latest... Read more »
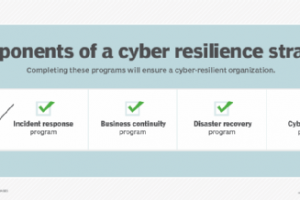
Business continuity plans ensure data availability and maintain operations during disasters and downtime. Downtime mitigation is a requirement for every organization, and a strong business continuity plan is key to maintain or... Read more »

A Russian cyber attack group has been targeting politicians, journalists, and military and intelligence officials across Britain and Europe for at least seven years, and may have stockpiled access to and data... Read more »

In October, Germany-based PoINT will launch an object storage archiving product based on disk and tape media. “Our idea is to offer on-site exactly the same thing as AWS [Amazon Web Services]... Read more »

The National Crime Agency (NCA) received a warrant to covertly harvest hundreds of thousands of messages from the EncroChat encrypted mobile phone network, on the basis of a conversation between a French... Read more »

The biggest factor impacting the evolution of application security is the speed at which technology changes. Much of this is due to widespread consumerisation – people expect new technologies and updates to... Read more »
What is a Google dork query? A Google dork query, sometimes just referred to as a dork, is a search string or custom query that uses advanced search operators to find information... Read more »

The National Crime Agency “deliberately concealed” information when it applied for a warrant to access hundreds of thousands of intercepted messages and photographs from the EncroChat encrypted mobile network, a court has... Read more »
