
Microsoft’s September Patch Tuesday update arrived on schedule late on 13 September, and this month contained five critical common vulnerabilities and exposures (CVEs) and one actively exploited zero-day, among a total of... Read more »

The UK’s Financial Conduct Authority (FCA) has revealed evidence of a dramatic and ongoing surge in the number of distributed denial of service (DDoS) attacks against the financial sector, with a quarter... Read more »

The death last week of Queen Elizabeth II at the age of 96, following a 70-year reign, has drawn global attention and may yet draw the focus of cyber criminal elements exploiting... Read more »

By What is data masking? Data masking is a method of creating a structurally similar but inauthentic version of an organization’s data that can be used for purposes such as software testing... Read more »
What is a computer worm? A computer worm is a type of malware whose primary function is to self-replicate and infect other computers while remaining active on infected systems. A computer worm... Read more »

It takes an average of just three steps for a threat actor to infiltrate a target cloud environment and get to its “crown jewel” assets, and as a result, vast numbers of... Read more »

Researchers at Secureworks’ Counter Threat Unit (CTU) have warned of a new and potentially serious vulnerability affecting the pass-through authentication (PTA) hybrid identity authentication method used in Azure Active Directory (AD). PTA... Read more »

Internal Cisco data leaked late last week by the China-based Yanluowang ransomware operation has been confirmed as stolen during a cyber attack earlier in 2022, but has insisted the leak poses no... Read more »

TA453, an Iran-aligned advanced persistent threat (APT) group, is going to increasingly complex lengths to compromise its targets, adopting a technique informally known as multi-persona impersonation (MPI) in the social engineering playbook... Read more »
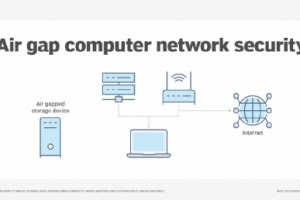
What is an air gap? An air gap is a security measure that involves isolating a computer or network and preventing it from establishing an external connection. An air-gapped computer is physically... Read more »
