
A cross-party group of MPs has called on the government to ban the sale and operation of CCTV surveillance cameras linked to human rights abuses in China. Surveillance cameras supplied by the... Read more »

The global cyber insurance market is set to be worth US$20bn in 2025, according to researchers at Statista. That is up from just under $8bn in 2020. Cyber insurance is now a... Read more »

Julian Assange has filed an appeal against the Home Secretary’s decision to extradite him to the US to face hacking and espionage charges. The appeal comes two weeks after Priti Patel signed... Read more »

The increase in remote working during and after the pandemic has greatly increased cyber vulnerabilities. With the cost of cyber breaches growing (globally, the average cost of a serious breach was $3.9m... Read more »

The UK’s newly-appointed information commissioner, John Edwards, has written to public sector bodies across the UK to set out a revised approach to how the Information Commissioner’s Office (ICO) works with the... Read more »
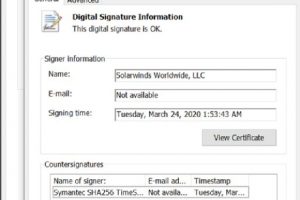
2020 was a roller coaster of major, world-shaking events. We all couldn’t wait for the year to end. But just as 2020 was about to close, it pulled another fast one on... Read more »

A relatively new data extortion operation going by the name RansomHouse appears to have turned over the systems of semiconductor specialist AMD, stealing more than 450GB of the organisation’s data and holding... Read more »

Researchers at Bitdefender Labs have published research into a widespread online dating scam that is exploiting its victims with the promise of romantic connections and even relationships with women in war-torn Ukraine.... Read more »

The security and intelligence services will have to obtain independent authorisation before accessing citizens’ private phone and internet records during criminal investigations following a landmark High Court decision. Two High Court judges... Read more »
What is hardware security? Hardware security is vulnerability protection that comes in the form of a physical device rather than software that’s installed on the hardware of a computer system. Hardware security... Read more »
