
The latest “technology pulse” poll from EY reports that 78% of tech executives are more concerned about the cyber security threats of today than those of a year ago. Those IT leaders... Read more »

Extreme Networks has disclosed that it is the latest technology company affected by the fast-developing MOVEit cyber attack, with downstream customers of the network hardware and services supplier potentially at risk of... Read more »
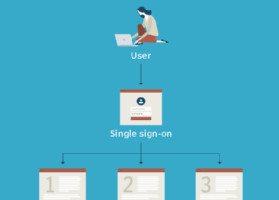
What is a logon (or login)? In computing, a logon is a procedure that enables an entity to access a secure system such as an operating system, application, service, website or other... Read more »

Organisations operating Barracuda Networks’ Email Security Gateway (ESG) appliances vulnerable to a bug tracked as CVE-2023-2868 to throw away their hardware, regardless of whether or not they have patched it, and seek... Read more »

The UK and US are moving closer to an agreement that will facilitate the free flow of personal data across the Atlantic, which Westminster hopes will speed up processes for businesses, reduce... Read more »

The University of Manchester in northern England has been hit by a cyber attack that appears to have resulted in the exfiltration of an as-yet unknown quantity of data. In a statement,... Read more »

Buying enterprise software is an expensive and risky endeavor, which is why software buying teams need to understand the subtle differences between a request for information, a request for proposal and a... Read more »
Driven by significant cyber security disclosures affecting supply chain dependencies, such as Log4j and Realtek, threat actors have vastly increased their use of vulnerabilities as a means to work their way inside... Read more »

Crypto firms that want to market their products in the UK will need to introduce new measures to protect consumers from rogue operators, including a cooling-off period for first-time buyers and an... Read more »

The threat actors behind the Clop (Cl0p in some variants) cyber crime gang currently holding the likes of British Airways (BA), Boots and the BBC to ransom may have discovered the MOVEit... Read more »
