Instead of keeping Secrets in Kubernetes manifests, store them separately. Portainer makes this quite simple; I’ll show you how in this tutorial.

When you’re building and deploying Kubernetes services and pods, you sometimes have to use a secret, such as a password, an API key or a third-party access token. You certainly don’t want to save those bits of sensitive information in your manifests, as doing that could lead to security issues. Given how many moving parts make up a Kubernetes deployment, the last thing you need is to extend your attack plane further.
SEE: Hiring kit: Back-end Developer (TechRepublic Premium)
How do you create and manage Kubernetes Secrets? If you’re using Portainer as your Kubernetes management platform, you’re in luck, as it includes a very powerful Secrets feature. In this tutorial, I’ll show you how the Portainer Kubernetes Secrets tool can make your life a bit easier.
Jump to:
What you’ll need to create a secret in Portainer
To follow along, you’ll need a running instance of Portainer and a user with deployment privileges. You’ll also need a secret to save.
How to create your first Kubernetes secret in Portainer
The first thing you’ll need to do is log in to your Portainer instance. Once you’ve logged in, select your Kubernetes environment, which will probably be listed as Local. From the left navigation, click ConfigMaps & Secrets (Figure A).
Figure A
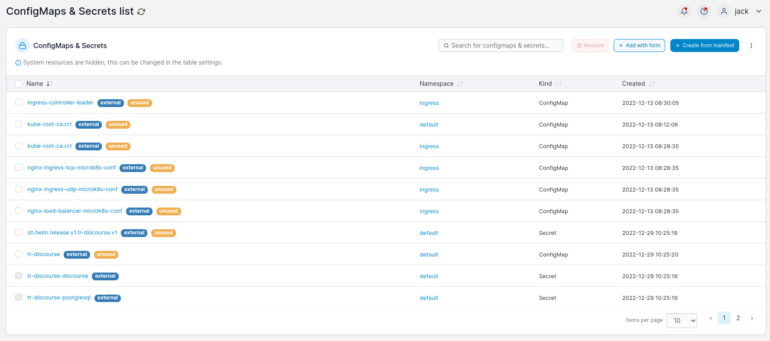
In the resulting page (Figure B), click Add With Form near the upper-right corner.
Figure B
In the next window (Figure C), click the Secret tab near the middle of the page.
Figure C
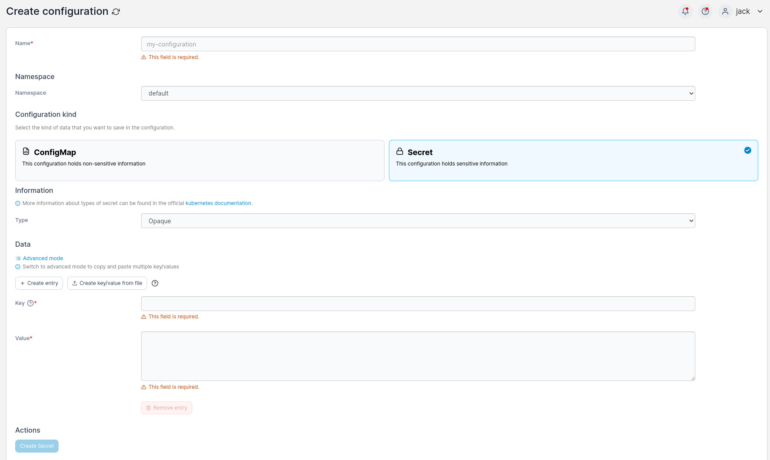
Here’s the information that you’ll want to include for your new secret:
- Name: A human-readable name for your secret.
- Namespace: The namespace for which the secret will be used.
- Key: The portion of the key pair that defines the first value, such as username.
- Value: The portion of the key pair that defines the second value, such as the password or access token — for example, if credentials are admin/@dm1n, admin is the key and @dm1n is the Value.
You an also select the Type, which can be one of the following:
- Opaque.
- Service account token.
- Dockercfg.
- Dockerconfigjson.
- Basic auth.
- SSH auth.
- TLS.
- Bootstrap token.
- Custom.
For simplicity, let’s select SSH auth. Now, it’s important to know that some Type options will automatically fill out the Key portion. For example, if you select SSH auth, the Key portion will auto-populate with ssh-privatekey.
Now, it’s time to give the new key a name, select SSH auth for the type and then retrieve the SSH public key you want to add. This key will start with ssh-rsa, include a long string of random characters and end with USERNAME@HOSTNAME, where USERNAME is your local username and hostname is the hostname of the machine you’re working on.
If you’re using an SSH key that’s on a different machine, you’ll need to track it down. Once you have your SSH public key copied, paste it in the Value field. When you have all required information in place, you’ll then be able to click Create Secret to save the new key.
How to use the new key
Let’s say you’re creating a new application for deployment. If that’s the case, you’ll click Applications and then click Add With Form. In the application form, you’ll see the Configurations section (Figure D):
Figure D
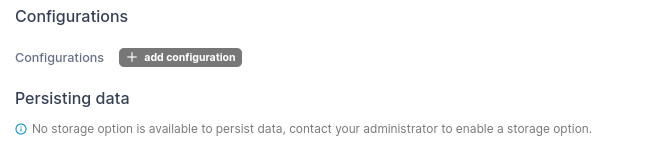
Click Add Configuration. In the resulting section, you’ll see a drop-down where you can select the newly created secret (Figure E):
Figure E
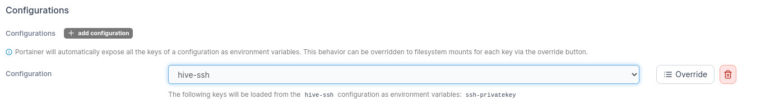
You don’t have to add any extra information for the secret, as Portainer will automatically map the entry to the key. With this step, you no longer have to add the secret to the manifest.
Kubernetes Secrets made easy
Secrets are a must-use, especially if you’re connecting any application to an API or third-party service. Thanks to Portainer, creating and using secrets for your Kubernetes deployments is incredibly easy.
SEE: Hiring kit: Platform engineer (TechRepublic Premium)
One thing to keep in mind, however, is that anyone on your Portainer system with the right privileges can view the secret. Be sure to grant user access to those environments wisely.
Read next: The 12 best IDEs for programming (TechRepublic)
